SSL notifications in Chrome and their meaning
This article is devoted to description of notifications appearing for SSL certificates in modern Chrome browsers (version 39+). Here is a list of the notifications we would like to expand on:
- Further, this page includes other resources which are not secure. These resources can be viewed by others while in transit, and can be modified by an attacker to change the look of the page.
- This site uses a weak security configuration (SHA-1 signatures), so your connection may not be private. <…> The certificate chain for this website contains at least one certificate that was signed using a deprecated signature algorithm based on SHA-1.
- Your connection to domain.com is encrypted using an obsolete cipher suit.
- No Certificate Transparency information was supplied by the server.
How to navigate to notifications in Chrome: click on the padlock or green bar > Details.
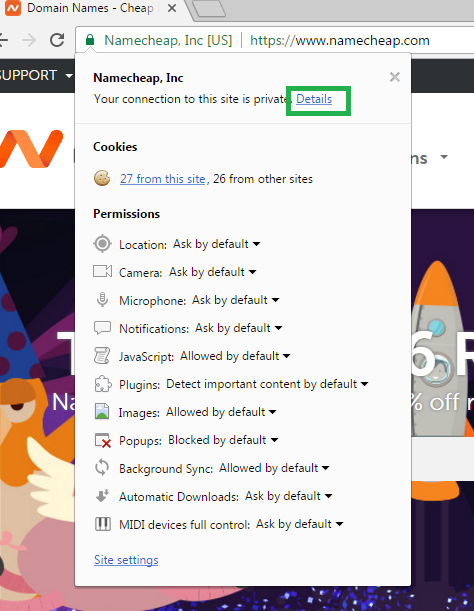
You will see the notifications on the right side of your screen.
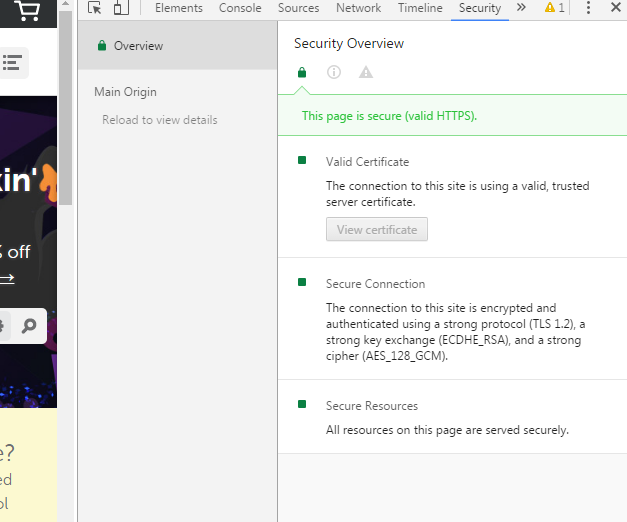
- The message “Further, this page includes other resources which are not secure. These resources can be viewed by others while in transit, and can be modified by an attacker to change the look of the page.” is often encountered after the SSL installation
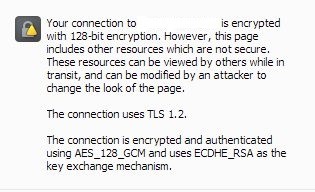
This is caused by HTTP links in the HTML code of the webpage. It is possible to check links in the browser, just press the combination Ctrl+ Shift + J (or Command+Option+J for Mac) and click Console. More information on this matter can be found here.
- The warning “This site uses a weak security configuration (SHA-1 signatures), so your connection may not be private. <…> The certificate chain for this website contains at least one certificate that was signed using a deprecated signature algorithm based on SHA-1.” appears for all certificates with the SHA-1 signature algorithm
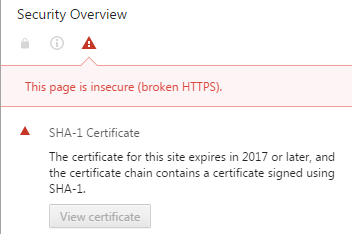
This issue is solved by the SSL certificate upgrade to SHA-256 with the help of a reissue process. The migration to the default SHA-256 with RSA signature algorithm for our certificates was performed on November 6, 2014.
- If you see the warning “Your connection to domain.com is encrypted using an obsolete cipher suit.”, your site is using a weak cipher suite or an SSL/TLS protocol to encrypt the traffic.
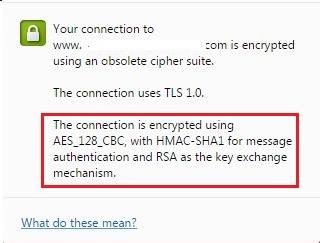
The green padlock is shown despite this message. Still, to be on the safe side it is better to disable weak ciphers and protocols on the server (e.g. SSLv2, SSLv3, RC4, SHA1 or MD5 hashes used for message authentication). It is possible to scan your website for detecting which cypher or protocol causes the warning using this analyzer. The root access is required to change the server configurations for disabling the weak ciphers, so if you have none, please contact your hosting/server provider for assistance.
- The message “No Certificate Transparency information was supplied by the server.“ concerns the Certificate Transparency Project. In this case the green padlock is also displayed by Chrome.
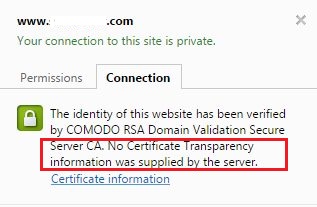
Certificate Transparency aims to monitor SSL certificates in real time, making issuance and use of fake SSLs almost impossible. The project should be implemented on the Certificate Authority side initially.
Among our SSLs only Extended Validation certificates support this project at the moment.
For the Domain and Organization Validation certificates the implementation of the Certificate Transparency feature is going to be implemented in the nearest future. Unfortunately, no ETA is available by the time being.
The following links might also be useful for you: